History of Encryption: Evolution from Ancient to Digital Age
Encryption is a technique used to hide information or true meaning from unwelcome eyes.
In history, encryption helped battle generals and soldiers secretly communicate with each other via different cyphers. In modern times, it allows us to protect our devices and personal information via passwords and encryption codes.
In this article, you will discover how encryption was used throughout history, how it’s used now, and what you could expect in the future.

Adomas Šulcas
9 min read
The History of Encryption: Ancient Civilizations
It’s natural that the history of encryption originated nearly after people invented writing. Some things are only meant to be read by certain people, and one way to do that is through ciphers.
Caesar Cipher (Rome)
Julius Caesar invented a substitution cipher where each letter is replaced by another. His method was based on each letter being replaced by one that is 3 letters up. For example, “A” means “D”, “G” means “J”, and “R” means “U”.
This technique allowed Caesar to send coded messages to his generals without curious eyes ever understanding the message.
Example: “Attack the left wing first” encrypted in Caesar cipher would become “Dwwdfn wkh hdvw zlqj iluvw”
Scytale (Sparta)
Used by the Spartans, a Scytale is an encryption device made of a cylinder and stripped parchment wrapped around it. Messages were only clear if the parchment was wrapped around a cylinder of the same size.
To decrypt it, you need to arrange the ciphered text into columns and read across the rows. For example, if the cylinder has 5 rows, a hidden message saying “they took us hostage” would look like this: “tohghokoesustya”.
The main use case for Scytales was to exchange secret messages during battles.
Encryption in Ancient Egypt and Mesopotamia
Ancient Egypt marks the beginning of the history of cryptography. Egyptians were the first people to discover a written way to keep secrets — hieroglyphics.
Hieroglyphic scripts and cuneiform are great examples of how people used to store information under complex symbols that not everyone could read. These hieroglyphics kept anyone outside the inner circle from understanding the messages and protected their privacy.
In simple terms, if you couldn’t understand the hieroglyphic images, you couldn’t get any information from them.
Use Cases in Warfare and Diplomacy
In the ancient times, encryption and coded messages were mostly used for wars, battles, and diplomatic communications. It used to be rather easy to intercept and steal messages from the opposition, which made encryption extremely important for successful battle strategies and tactics.
Diplomatic relations were equally important as well. New alliances between states or cultures could seriously change the power dynamics. Therefore, it was essential for interested states to keep the terms of the treaties hidden from rival parties.
Encryption in the Medieval Period
Advancements in Cipher Techniques
During the Medieval period, the Polybius Square encryption was among the most used ciphers. It involved a 5x5 table which contained all the letters of the alphabet (sometimes combining “I” and “J” to fit in 25 squares). Each letter was identified by its row and column number.
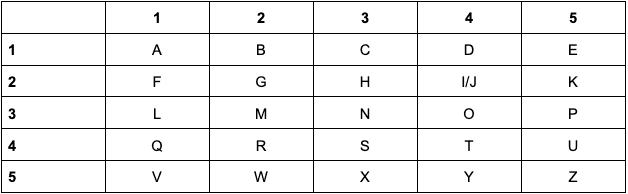
Encrypting the message is simple: write the number combinations instead of letters. For example: “King is dead” would transform to “25 24 33 22 24 43 14 15 11 14”.
Encryption in Religious and Political Contexts
The Medieval times were dense in terms of religious conflicts. As a result, various religious documents, manuscripts, and other literature had to be protected. Encryption methods were mostly used to keep sensitive information secure and to prevent outsiders from corrupting and misinterpreting the prophecies.
In political espionage, intercepted messages could change the course of a conflict entirely: from potential alliances and military strategies to betrayals and weapon shortages. Therefore, it was essential to encrypt the messages in case rivaling powers get ahold of them.
Renaissance Encryption: The Birth of Complex Ciphers
The Vigenère Cipher
The Vigenère Cipher was the first cipher in the world that resisted frequency analysis. In turn, this made it significantly more secure than simple substitution ciphers like Caesar’s.
Here’s how it works:
- Keyword. The cipher uses a keyword to control letter shifts.
- Message encryption. The message is encrypted by shifting each letter by a specific number of positions in the alphabet. The number is determined by the corresponding letter in the keyword.
For example, the message you need to encrypt is “attack”, and the selected keyword is “lemon” (could be any word).
The word “attack” has 6 letters, while the keyword has only 5. To make this cipher viable, we need to repeat the keyword until the total number of letters match the message. In this case, the keyword changes to “lemonl”. If the message had 9 letters, the keyword would change to “lemonlemo” and so on.
The encryption works like so:
- A (shift by L) → L
- T (shift by E) → X
- T (shift by M) → F
- A (shift by O) → O
- C (shift by N) → P
- K (shift by L) → V
Result: “attack” = “LXFOPV”
To simplify the logic: if K is the 11th letter in the alphabet, and L is the 12th letter in the alphabet, then the cipher will be the 12th letter in the alphabet, counting from K (K included).
This cipher is a major milestone in cryptography and it became known as “le chiffre indéchiffrable” (the indecipherable cipher) because it was only cracked in the 19th century by Charles Babbage and Friedrich Kasiski.
Leon Battista Alberti’s Contributions
Leon Battista Alberti, also known as the father of Western cryptography, is an inventor of the cipher disk, which enabled polyalphabetic substitution.
The disk consisted of two rotating circles. The outer disk contained the alphabet in a fixed position, while the inner disk could be rotated to set different ciphers. Each time the disk was rotated, a different substitution cipher was used. This way, substitution ciphers became significantly more secure, since every few letters you could use a different substitution cipher.
Influence on Renaissance Espionage
The Italian Wars are a great example of encryption’s influence on Renaissance Espionage. These wars involved a series of conflicts between France, Spain, the Holy Roman Empire, various Italian states, and some other European powers.
Naturally, monarchs wanted to gather and intercept information from rival powers about troop movements, diplomatic strategies, potential betrayals, and other competitive intelligence. As a result, several Italian states frequently used ciphers to communicate with their ambassadors stationed in enemy territory.
To secure these communications, they mostly used the Vigenère cipher and some simpler monoalphabetic ciphers.
The Evolution of Encryption in the Early Modern Era
Advancements in Cryptanalysis
The frequency analysis, developed in the Arab world, was already widely used by the time of the Renaissance. It became the key method (pun intended) for breaking ciphers. In essence, this method put an end to simple substitution ciphers and forced society to come up with more complex ciphers that didn’t depend on frequency.
Case Study: Mary, Queen of Scots
Mary, Queen of Scots, used encryption to conspire the assassination of Queen Elizabeth I. However, the encryption strategies used were relatively old and the Queen’s spymaster was able to crack the code using frequency analysis. Eventually, Mary was convicted of treason and executed.
20th Century: The Age of Machines and War
World War I Encryption
During World War I, everyone relied on basic encryption methods such as field ciphers and codebooks to protect battle messages. However, these methods were quite simple to intercept and decrypt.
As a result, it kickstarted the development of more complex encryption systems by the end of the war, and during World War II Nazi Germany had an extremely sophisticated system that will be remembered in the encryption history for a long time – the Enigma Machine.
The Enigma Machine
The Enigma Machine was the most sophisticated and complex cipher device to date during World War II. It was used to encrypt military communications and had an enormous number of possible settings.
This cipher device was an electromechanical rotor mechanism and cracking the code would have required 17,000 different combinations in the span of 24 hours. However, Polish cryptographers led by Alan Turing managed to break the code, which significantly helped Allies win the war.
After this effort, cryptography got recognized as a science and Alan Turing was inspired to create a computer focused on breaking encrypted messages.
The Birth of Modern Cryptography
The advent of early computers revolutionized cryptography forever. A new age has begun where decrypting the messages no longer relied on human effort. Machines could process and store vast amounts of data, allowing them to break complex ciphers and set the stage for modern cryptography based on algorithms.
Additionally, various other attack methods have emerged that could potentially compromise data security. Encryption keys can be leaked, or the devices themselves may become infected with malware, for example. Learn how to know if your computer has a virus to protect from such threats.
Modern Encryption: The Digital Revolution
Public-Key Cryptography
Public-key cryptography revolutionized encryption by allowing secure communication between parties without a shared secret key. RSA and Diffie-Hellman protocols introduced the concept of key pairs: one public and one private. This enabled secure data exchange and digital signatures.
Encryption in the Internet Age
Protocols like SSL/TLS ensure secure communication on the internet. It encrypts data between the user and the server. HTTPS uses these protocols to secure web traffic which, in turn, protects users’ sensitive data like passwords, card details, addresses, and other information.
VPNs use these SSL/TLS encryption protocols to secure your internet connection. They create encrypted tunnels that protect user data from eavesdropping and hacking on public or unprotected networks. You can learn more about it in our internet connection encryption guide.
Cryptographic Algorithms
There are 2 main cryptographic algorithms: AES (Advanced Encryption Standard) and SHA (Secure Hash Algorithm). AES is widely used for encrypting sensitive data and in network protocols, such as WPA2 vs WPA3. SHA is crucial for data integrity as it generates hash values to verify the authenticity of data in blockchain, digital signatures, password storage, and more.
Encryption in the 21st Century and Beyond
Quantum Cryptography
Quantum computing poses a major threat to traditional encryption methods like RSA. Quantum cryptography offers QKD (Quantum Key Distribution), which aims to secure data by utilizing the principles of quantum mechanics. This means theoretically unbreakable encryption.
Blockchain and Encryption
Blockchain technology relies on encryption for secure and untampered transactions. Secure Hash Algorithm (SHA) ensures the integrity of data, while public-key cryptography allows for secure digital signatures and authentication. It makes blockchain the backbone of decentralized applications.
Future Trends in Cryptography
Future cryptography will likely focus on post-quantum cryptography to defend against the mentioned “theoretically unbreakable” quantum threats. Also, AI and ML will probably enhance all encryption and hacking efforts, leading to a continued race between cybercriminals and cybersecurity.
So, the question of why use a VPN encryption is likely to remain debated. Authoritarian governments will continue to limit VPN use, and privacy enthusiasts will find new workarounds. It's already happening as users need to check are VPNs legal in their countries before connecting.
Ethical and Legal Implications
The discussion between encryption and privacy does not appear to be at rest. Governments seek access to encrypted data for national security reasons, while privacy institutions have their own arguments. Backdoors and mandatory decryption raise concerns over privacy rights, with continuous legal battles over the balance between security and civil liberties.

Author
Adomas Šulcas
Chief Operating Officer at Growth Bite
Adomas is a technical writing expert who founded Growth Bite, a digital marketing company, focused on providing high-value SEO and content marketing services to SaaS companies.
Related articles
4 min read
Best Residential VPN Providers in 2025
A Virtual Private Network (VPN) encrypts your traffic and hides your IP address. The way these functions are accomplished affects various aspects of your online privacy and security.
Here, we'll consider using residential IP addresses instead of those originating from a data center. A residential VPN has advantages compared to traditional ones, but there are some caveats. It all boils down to residential VPN providers.
The worst ones may even create more risks than benefits. We'll end this article with a list of the best residential VPN providers on the market.

Guoda Šulcaitė
4 min read
Ethernet vs Wi-Fi: Which One is Better?
Ethernet and Wi-Fi are the two main ways to connect your computer to the internet. While Wi-Fi has received significantly more attention in recent years, especially among consumers, due to its simplicity and flexibility, ethernet is still widely used in various other applications.
Even if Wi-Fi is significantly more popular, it isn’t strictly better. Both methods have their benefits and drawbacks. Wi-Fi’s popularity comes from its ease-of-use and flexibility, but an ethernet connection can be much more useful in certain scenarios.

Adomas Šulcas

5 min read
How to Change Chrome Proxy Settings: The Ultimate Guide
A proxy server is an easy alternative to a VPN that can perform most of the functions of the latter. It’s a server that stands between your device and the destination server, taking your connection requests and forwarding them in your name.
Destination servers in almost all cases see the proxy server as the originator of the request. As such, proxies are widely used in various, mostly business-related applications whenever privacy, security, location changing, and several other factors are at play.

Guoda Šulcaitė